By Seán Boran
December 13, 1999. This article presents an overview of corporate information security, not just in a computer/network context, but also considering social and physical aspects.
Checklists are provided to stimulate analogies in your own corporate environment.
We welcome your feedback on this article.
Security involves prevention, detection, response, monitoring and review measures to reduce perceived risks to acceptable levels. These measures need to be uniform and continuous in domains such as Social/Personal, Computer/Network and Physical.
This article divides up explanation of corporate information security into:
Understanding corporate security is about understanding what the key assets in the company are. Today, the key asset is often information. But information alone is not enough, knowledge of how to use valuable information is needed to provide a competitive edge. The value of information may depend on being secret and accurate.
Information can take many forms, hence methods of securing information are various.
Instead of dividing information into categories based on content, consider analysing
threats to information (and hence its protection) on categories based on methods of
processing / storing.
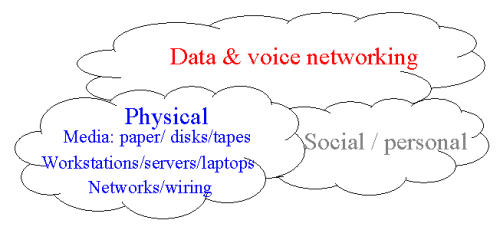
Three "information domains" are defined:
 |
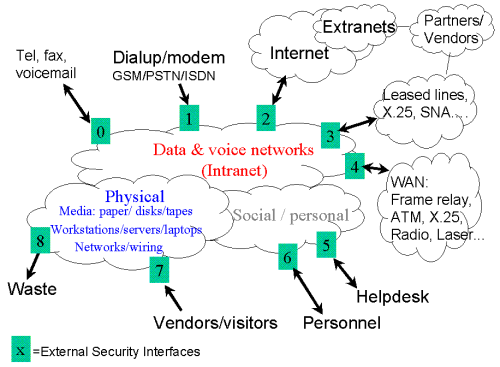
Each of these domains contains interfaces to the outside world.
 |
This may look overwhelming at first, lets look at the domains one by one.
The Buzzwords are explained at the end of the article if they are new to you - don't
worry, they're just networking technologies.
The numbers in brackets below refer to numbered interfaces above.
(0) Telephone/voicemail systems are increasingly complex and may interface to the Intranet.
(1) Dialup modems (whether analog, digital or radio) remain the predominant access method for teleworkers and IT Support staff to remotely access corporate data.
(2) The Internet, a public network of (thousands of) networks, is fast becoming the preferred media for information exchange whether via World Wide Web, Email or Extranets (encrypted virtual networks on the Internet).
(3) Large corporations have many links to partners and vendors, often using many different technologies and implemented too quickly for security to be properly considered. These vendors/partners in turn, have further links to the Internet etc.
(4) The Corporate Intranet may extend across several cities and even countries.
Different technologies can be involved in the many transport layers, from fibre or copper
cables, ATM switches to the familiar TCP/IP protocols.
The domain interfaces can be subject to various types of threats, for example:
(0) Telephone/voicemail security is often forgotten about, threats involve attackers telephoning cheaply internationally, listening to voicemail messages and possibly unauthorised access to the Intranet (if an interface to the Intranet exists).
(1) Dial-up networks can be an easy entry point for attackers, as they are often less well protected or monitored than Internet connections. Typical attacks are identity spoofing leading to unauthorised access. Analog connections are easier to eavesdrop.
(2) The Internet connection offers a way to communicate with millions of people globally, but is difficult to control due to it's complex and dynamic nature. A wide range of attacks are possible: eavesdropping, identity spoofing, denial of service.
(3) Connections to vendors/partners are often not secured enough, due to lack of
time/resources, or belief in security through obscurity. They can be used as an attack
point by Partner organisations (Partners don't always stay partners...) and also for
attackers who have already penetrated the Partner's network.
Threats: unauthorised access, denial of service.
(4) Wide area networks are used to extend the corporate Intranet to many remote areas. The cabling probably passes through public zones. The complexity of Wide Area Networks can serve as a deterrent to attackers, but is it enough? How much can you trust network providers? The main threats are eavesdropping, denial-of-service and possibly identity spoofing.
(5) Social engineering can be used to trick personnel into divulging information or providing access.
(6) Helpdesks may also be subject to social engineering, providing modem numbers, passwords etc. unwittingly to unauthorised persons.
The other key threats are misuse of privileges, illegitimate use and mistakes.
(7) Many people who are not employees, will have access to buildings in one way or another. Threats include theft, damage and copying.
(8) Sensitive information, if not securely disposed of, will yield a valuable resource to attackers. The main threat is unauthorised access to information.
Other physical threats include laptop theft, natural disasters and loss of media during transport.
These threats can result in critical information being lost, copied, deleted, accessed
or modified, or services no longer functioning (loss of confidentiality, integrity or
availability).
Before deciding on safeguards to counter the threats listed above, consider:
The nature of the threat. The attackers resources (financial, technical, time), degree of motivation and ease of access should all be considered. For example, most would expect frequent attacks from the Internet, so firewalls between the Internet and Intranet are frequent. The media often remind us of the exploits of crackers, but what of the disgruntled employee, who has access to critical systems for his daily work? What of the manager who has a gambling habit and is tempted to embezzle to pay debts? Whereas attacks from Internet Crackers may be frequent and technically interesting, they are rarely as financially damaging as deliberate misuse of systems by employees.
Information lifetime. How is information generated, stored, processed, copied, printed and destroyed?
Information aging. How does time affect the information? e.g. a new pricelist might be sensitive before publication and would published to the world subsequently. A new pricelist replaces an old one, becomes useless.
Nature: The likelihood of natural disasters.
Security Measures are needed to reduce risks to an acceptable level. If we assume that a possible attacker is external to the organisation, possible measures that could be taken in each of the interfaces (listed in green in the diagram above) are;
Measures for Logical or Network Interfaces:
Technical mechanisms:
- Authentication of users and/or computers
- Encryption to protect privacy or for authentication
- Digital signatures for authenticity and no-repudiation
- Access control
- Resource isolation: By isolating services from each other, a weakness or abuse of one service may not necessarily lead to abuse of other services.
- Virus/malicious content controls
- Hardening: secure installation/configuration
- Reliability measures: backups, redundancy, hot spares, clusters, RAID, maintenance contracts, off-site copies, contingency planning.
- Monitoring
The following is a list of mechanisms relevant to specific Interfaces. Note that hardening, resource isolaton, reliability measures and monitoring/auditing are useful on all interfaces.
(0) Authentication
(1) Strong authentication of users, possibly encryption
(2) All mechanisms
(3) Authentication of users or computers, access control, possible encryption.
(4) Encryption
Measures for Social / Personal Interfaces:
- Definition of security policies, to protect assets based on the risk. A security policy is a preventative mechanism for protecting important company data and processes. It communicates a coherent security standard to users, management and technical staff.
- Information security education of users / managers / system administrators.
- Tools to enable users to implement policy.
- Strong passwords, screen locks.
- Person authentication, inquisitiveness, monitoring/auditing.
- Organisation: Roles, responsibility and procedures are required to ensure that policies are implemented. A security organisation can reduce risk and limit damage by providing users with a central point for reporting, for handling of incidents and allocation of security responsibilities.
Measures for Physical Interfaces:
- Limit access: locked rooms/entrances, physical zones, identification badges.
- Keep a record of accesses.
- Shredding/secure destruction/recycling.
- Insure against loss.
- Laptop access control/ encryption tools.
- Resource isolation.
- Availability: backups, (off-site) redundancy, etc.
Assurance / constant vigilance:
- Reconsider risks regularly. Are new threats more important, have some threats ceased?
- How effective are the countermeasures, do they require tuning?
- Conduct regular audits of important systems/interfaces.
On the other hand, if the primary source of attack is expected to be internal (whether malicious or accidental), the focus changes, since attackers might be authorised to bypass access control mechanisms:
Security measures will improve security properties, such as
Assurance: Confidence that security measures are correctly implemented and that a system will behave as expected.
Identification / Authentication: When users or programs communicate with each other, the two parties verify each other's identity, so that they know who they are communicating with.
Accountability/Audit Trail: The ability to know who did what, when, where. Users are responsible and accountable for their actions. Automatic audit trail monitoring and analysis to detect security breaches.
Access Control: Access to specified resources can be restricted to certain entities.
Object Reuse: Objects used by one process may not be reused or manipulated by another process such that security may be violated.
Accuracy / Integrity: Objects (information and processes) are accurate and complete.
Secure information exchange: Information transmitted adheres to expected levels of authenticity, confidentiality, and non-repudiation.
Reliability / Availability: Information and services are available when needed.
Knowledge and information are the most important assets of many companies, they need protecton. Information can take many forms, hence methods of securing information are various.
Consider analysing threats to information based on:
Coordinated Countermeasures should help provide a continuous, uniform level of secuity that reduces risks to an acceptable level:
| URL | What you type in a Web Browser to get to a site (Uniform Resource Locator) |
| UNC | The way Microsoft names network file shares (Uniform naming convention) |
| Security | is protection of Assets (information, systems and services) against disasters, mistakes and manipulation so that the likelihood and impact of security incidents is minimised. |
| Confidentiality | Sensitive business objects (information & processes) are disclosed only to authorised persons. |
| Integrity | The business need to control modification to objects . |
| Availability | The need to have business objects (information and services) available when needed. |
| Threat | is a danger which could affect the security (confidentiality, integrity, availability) of assets, leading to a potential loss or damage. |
| Risk | is a measurement of the severity of threats. |
| Access control | The prevention of unauthorized use of a resource, including the prevention of use of a resource in an unauthorized manner. |
| security policy | The set of laws, rules and practices that regulate how assets including sensitive information are managed, protected and distributed within an organisation or specific IT system(s). |
| ATM PSTN ISDN GSM X.25 SNA WAN Frame relay |
Networks & protocols Asynchronous transfer mode Normal analog phone lines: (public subscriber telephone network) Digital phone lines: Integrated digital services network Digital mobile radio: Global Services Mobile (from french expression) Digital data lines (ISO standard) IBM networking protocols (Systems Network Architecture) Wide area network A WAN technology used mostly by Telecoms carriers |
Other glossaries:
SANS Glossary of Terms Used in Security and Intrusion Detection http://www.sans.org/resources/glossary.php
| Title | Author |
| A Code of Practice for Information Security Management BS7799, ISBN 0-580-22536-4 www.privacyexchange.org/buscodes/standard/bsi.html dtiinfo1.dti.gov.uk/security/approach.htm www.dti.gov.uk/CII/bs7799/ |
British Standards organisation (BSI) 1993 |
| IT Baseline protection manual www.bsi.bund.de/gshb/english/menue.htm |
German BSI |
| "European Orange Book" ITSEC Information
Technology Security Evaluation Criteria www.itsec.gov.uk/docs/introgds.htm www.itsec.gov.uk/docs/formal.htm#ITSEC |
EC: F/GB/D/ NL June 1991 |
| TCSEC "Orange Book" & Common Criteria www.radium.ncsc.mil/tpep |
DoD |
| Computer Assurance Guidelines www.lowpay.gov.uk/cag/contents.htm |
DTI |
| EPHOS Security Services www.nethotel.dk/ephos/en/booku/i3utoc.htm? |
EPHOS |
Seán Boran is an IT security consultant based in Switzerland and the author of the online IT Security Cookbook.